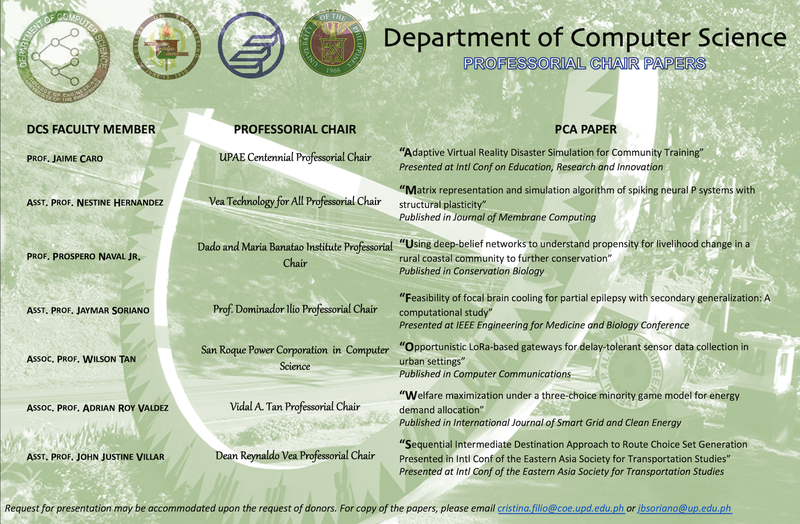
DCS Professorial Chair Colloquium to be held on October 26, 2020 (online)
The Department of Computer Science is pleased to announce that its yearly Professorial Chair Colloquium will be held this October 26, 2020, Monday, via an online (Zoom) session. The Professorial Chair Colloquium is an annual event where professorial chair awardees talk about their research projects and activities, and showcases some of the Department's latest research efforts.
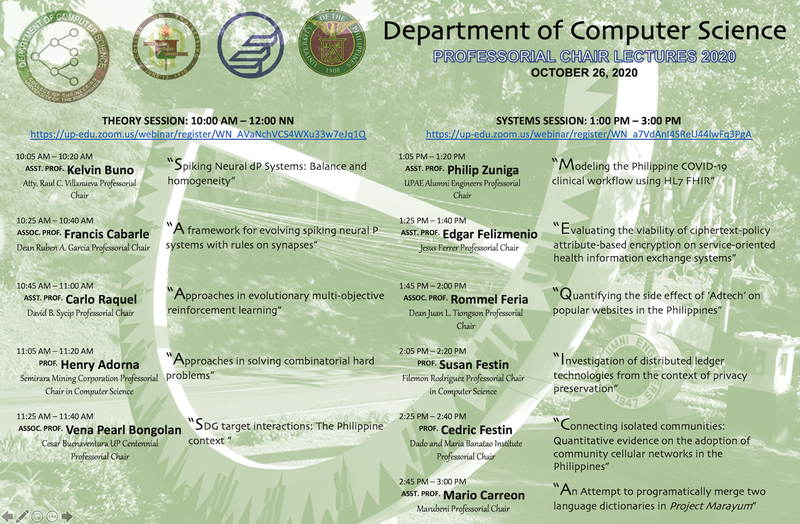
To register, follow the links below -
*Theory Session (10am -12:00nn)*
Register in advance for the morning session:
https://up-edu.zoom.us/webinar/register/WN_AVaNchVCS4WXu33w7eJq1Q
*Systems Session (1:00pm-3:30pm)*
Register in advance for the afternoon session:
https://up-edu.zoom.us/webinar/register/WN_a7VdAnI4SReU44lwFq3PgA
After registering, you will receive confirmation emails containing information about joining the webinars.
DCS Professorial Chair Lectures
Abstract of Talks
Spiking Neural dP Systems: Balance and homogeneity
This work explores some properties of Spiking Neural dP Systems, namely: (1) balance and, (2) homogeneity. This class of Spiking Neural dP Systems uses Extended SNP systems with Request Rules. As a case study, this work presents two SNdP systems that accept a language where these SNdP systems differ in the balance of the input partition, the homogeneity of components of the system, or the number of SNP components. An analysis of the communication cost and running time is given for the two presented SNdP system.
A framework for evolving spiking neural P systems with rules on synapses
In this paper, we present a genetic algorithm framework for evolving Spiking Neural P Systems with rules on synapses (RSSNP systems, for short). Starting with an initial RSSNP system, we use the genetic algorithm framework to obtain a derived RSSNP system with fewer resources (fewer and simpler rules, fewer synapses, less initial spikes) that can still produce the expected output spike trains. Different methods in the selection of parents and in the calculation of fitness are incorporated. We also try the framework on 5 RSSNP systems that compute bitwise AND, OR, NOT, ADD, and SUB respectively to gather data on how the framework behaves. Lastly, we discuss the asymptotic complexity of the algorithm and its effectiveness in generating fitter RSSNP systems based on which methods were used.
Approaches in evolutionary multi-objective reinforcement learning
A recent trend in machine learning is borrowing ideas to and from the field of optimization. We can find this novel symbiosis in Reinforcement learning (RL) and Evolutionary Computation (EC) where both EC and RL solves an optimization function. The marriage of multi-objective optimization (MO) and RL is called Multi-objective Reinforcement Learning (MORL) where methods from MO are incorporated into RL to develop algorithms to learn Pareto optimal policies. EMORL optimizes reward vectors instead of reward values. Only few multi-objective RL algorithms have an evolutionary component and they are called evolutionary multi-objective reinforcement learning (EMORL) and can be classified according to the type of RL: evolutionary MO for direct policy search, scalarization functions, evolutionary MO for value function approximations, hypervolume-based search and multi-objectivization. While these approaches are novel, they inherit some problems from MO such as being unable to scale up with the number of objective functions. In this paper, we provide the current state of the field of EMORL and identify research directions for the field.
Approaches in solving combinatorial hard problems
This is the continuation of the reports on “ Some combinatorial hard problems and algorithmic solutions" presented during A.Y. 2018-2019. We report on the improvements made on Poset Cover problem. Continuation of the efforts in using heuristics to make sense of MCDS on PPI Networks is reported. We give a glimpse on the idea of re-optimization and P systems as another technique in solving NP hard problems.
SDG target interactions: The Philippine context
The United Nations developed the 17 Sustainable Development Goals (SDGs), with 169 total targets, to serve as a plan for solving the world’s problems and achieving a more sustainable future. This study aims to exhaustively analyze the intra-goal and inter-goal interactions between targets via a binary comparison that entails over 14000 comparisons, modelled as a graph with the targets as nodes, and with the interaction between targets as the edges of the graph. The problem is to assign a ‘color’ to an edge, as positive, zero or negative. With a panel of experts to evaluate the target interactions, a web application was developed for coloring the edges. Experts are required to have at least five years relevant experience among the fields of sustainability and development issues. The functionalities of the web application include administering the questionnaire to collect the interaction scores and insights from the respondents, presenting target interactions between chosen goals, and displaying the overall state of the network of target interactions. The network of interactions can help the researchers analyze which targets will enable or constrain each other, what mitigation can be done to avoid conflicts, or which targets can be beneficial to each other. The insight gained from this study can help guide the Philippines in its endeavor towards becoming a developed country. This study can also be configured for sub-national or regional study.
Modeling the Philippine COVID-19 clinical workflow using HL7 FHIR
Since the onset of COVID – 19 in the Philippines since January 2020, the country has revitalized its health care system to ensure that the workflows will be able to absorb the expected bulk of COVID-19 cases in the country. Several changes in reporting was made, and protocols on centralized reporting of COVID-19 cases are done. With the standardization of these templates, there is now a need to develop a way of submitting health data from source applications to centralized applications. In this study, we present a FHIR model on how the whole data reporting workflow can be represented.
Evaluating the viability of ciphertext-policy attribute-based encryption on service-oriented health information exchange systems
Achieving interoperability in healthcare leads to several benefits that affect consumers and other stakeholders. With this, several countries have already implemented a Health Information Exchange (HIE) to enable interoperability in their areas. OpenHIE [5] is an initiative that aims to address the interoperability challenges in underserved regions, such as third-world countries. OpenHIE provides a framework for implementing an HIE which is based on the Service-Oriented Architecture (SOA). Its design has been proven to work, and other countries and organizations have shown interest in adopting its components. Currently, OpenHIE can provide the de facto standard for securing health information systems. However, several essential security features concerning the privacy of health information have yet to be implemented. Here we explore the application of Ciphertext-Policy Attribute Based Encryption (CP-ABE) on OpenHIE to realize the security features. Results show that applying CPABE will not only change the implementation of the functionalities of the HIE, but it will also add an overhead to its non-functional characteristics, such as the number of transactions per second, memory, and bandwidth usage.
Quantifying the side effect of ’Adtech’ on popular websites in the Philippines
Online advertisement has existed ever since the commercialization of the web in the mid-1990s. The effects of having online ads on users merely annoyed them. However, as advertising technology evolves, the side effects of having online ads have become more serious, claiming privacy as its first victim. This paper attempts to reveal another side effect that users do not normally perceive, which is data wastage. Initial findings show an average of 35% savings on downloaded data when using Firefox or Safari when visiting the top five (5) websites in the Philippines.
Investigation of distributed ledger technologies from the context of privacy preservation
Distributed Ledger Technologies (DLTs) are now being considered for various applications. While the most popular DLT, the blockchain, started out as a means to enable cryptocurrency, we now see DLTs used in health records, financial transactions, and Internet of Things (IoT). However, this wide range of potential use of DLTs has exposed security issues not previously considered or relevant: the problem of safeguarding privacy and integrity in the context of a shared, and possibly public, ledger. In this paper, we review the different DLTs and identify the privacy and integrity risks inherent in a decentralized and shared ledger. Lastly, we present current efforts in the research community as to how some of these privacy risks may be mitigated. These mitigation mechanisms will allow the consideration of DLTs in more varied applications.
Connecting isolated communities: Quantitative evidence on the adoption of community cellular networks in the Philippines
What determines the success of community cellular networks? And who uses the network? We leverage unique circumstances where all households in seven localities were interviewed before the installation of cellular network towers. We observed substantial differences in network adoption across the seven project sites. Four sites displayed high and regular usage, while three sites displayed anemic usage after the initial week of network service. We show that social and economic factors correlate with cellular network adoption. Sixty-five percent of households in the project sites made or received at least one call on text message. Farming and fishing households, as well as female-headed households, were particularly likely to join the cellular network. Wealthier households initiated and received more calls and texts. Households with higher levels of education initiated and received more text messages. Our results provide evidence of the demand for cellular networks.
An Attempt to programatically merge two language dictionaries in Project Marayum
Project Marayum is DOST funded community-built mobile phone based online web dictionary for Philippine Languages. As part of the project's work with the Asi speaking peoples of Romblon, the team was able to get an English to Asi dictionary and a separate Asi to English dictionary. In this paper, we describe these two dictionaries, the attempts to consolidate, and the generation of a seed dictionary through pattern matching database search.